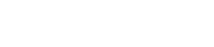Google Hacker Asks Apple to Donate $2.45 Million In Unpaid iPhone Bug Bounties
A Google security researcher says that he’s found 30 vulnerabilities in iOS that have made Apple’s software more secure—and he wants the company to pay up.
It is well known that “Apple’s iPhone is one of the most secure consumer device on the planet. But that hasn’t stopped a small dwindling group of hackers from finding flaws in it,” Lorenzo Franceschi-Bicchierai reports for Motherboard. “In 2016, Apple invited those hackers to report the bugs to the company, offering six figures rewards for their bugs, perhaps in an attempt to stop them from selling them to other high-paying startups.”
Project Zero is a Google undertaking that employs security researchers for finding bugs in software built by other companies. Google’s developers were responsible for identifying bugs in iOS and offered Apple 90 days to fix the bugs before they would be publicly disclosed. Apple patched the bugs, but Beer claims that Apple did a bad job at fixing them.
Black Hat security conference was held in Las Vegas on Wednesday, Beer tweeted a message to Apple’s CEO Tim Cook, challenging him to pay for each bug he has reported since 2016, and asking him to donate $2.45 million to human rights group Amnesty International.”
Apple spokesman declined to comment, and Beer could not be reached for comment.
“I’d love to get a chance to sit down with you and discuss how together we can make iOS even more secure for all our users. Cheers, Ian Beer,” he tweeted.
Beer is often featured in Apple’s security bulletins for his contributions finding flaws in iOS. Last year, he sent the jailbreaking community—a loose group of amateur hackers that dedicate their time to exploiting the iPhone—into a frenzy when he announced the upcoming release of a tool that would make jailbreaking iPhones relatively easier. Beer and Google came through a few weeks later, when they released the tool, which fellow iOS hackers saw as a significant step towards developing a full-fledged jailbreak.
Apple’s bug bounty program was lackluster at the start of last year. Most independent iOS security researchers did not submit any errors to Apple in exchange for a bug bounty, mainly because it would block future research and be too cumbersome, whereas the loopholes might be able to sell more money in the grey market.